Empowering Business Security Through Innovative Solutions
Revolutionizing Security Practices with Voice Pattern Technology
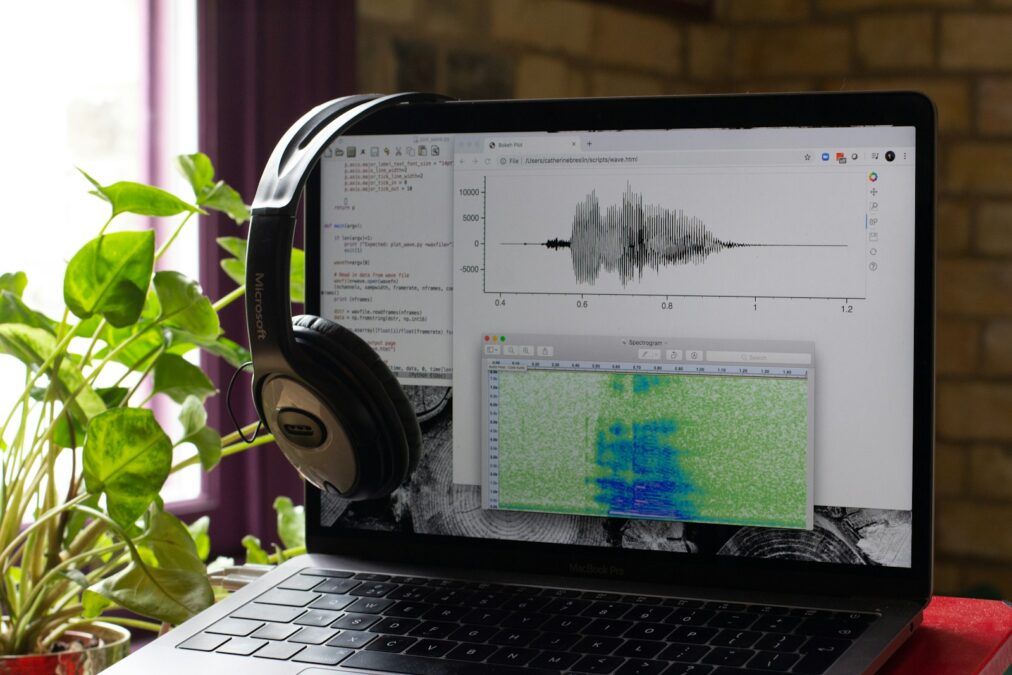
Embracing the latest advancements in security technology, businesses in Saudi Arabia and the UAE are turning to voice pattern technology to safeguard their digital assets and sensitive information. Voice pattern technology leverages the unique characteristics of an individual’s voice to authenticate their identity with unparalleled accuracy and reliability. By analyzing various aspects of speech, including tone, pitch, and rhythm, this innovative technology creates a distinct voiceprint that can be used to grant or deny access to secure systems and data.
The adoption of voice pattern technology represents a significant shift in security practices, offering businesses a more convenient and secure alternative to traditional authentication methods. Unlike passwords or PINs, which can be forgotten, stolen, or easily replicated, a person’s voice is inherently unique, making it an ideal biometric identifier. With voice pattern technology, organizations can strengthen their security posture while providing a seamless user experience for employees and customers alike.
Artificial Intelligence plays a crucial role in advancing voice pattern technology, enabling sophisticated voice recognition algorithms that can adapt to individual speech patterns over time. By continuously learning and refining its models, AI enhances the accuracy and reliability of voice authentication systems, reducing false positives and negatives. As businesses across Riyadh and Dubai embrace digital transformation, the integration of AI-powered voice pattern technology offers a proactive approach to cybersecurity.
Change Management Strategies for Successful Implementation
As businesses embark on the journey of adopting voice pattern technology for security purposes, effective change management strategies are essential to ensure successful implementation and user acceptance. Change management involves guiding individuals and organizations through the process of transitioning from familiar practices to new ways of working. In the context of security technology adoption, change management focuses on addressing employee concerns, overcoming resistance to change, and fostering a culture of trust and collaboration.
Management consulting firms specializing in change management can provide valuable support and guidance to businesses seeking to implement voice pattern technology. These firms offer expertise in organizational change, stakeholder engagement, and communication strategies, helping organizations navigate the complexities of technology adoption. By involving employees in the decision-making process and addressing their needs and preferences, businesses can increase buy-in and ensure a smooth transition to the new security solution.
Effective communication is also crucial throughout the implementation process, from the initial rollout of voice pattern technology to ongoing training and support. Clear and transparent communication helps to manage expectations, address concerns, and reinforce the benefits of the new security solution. By keeping stakeholders informed and engaged at every stage, organizations can build confidence in the technology and promote a positive security culture.
Leadership and Strategic Vision in Security Innovation
Leadership and strategic vision are essential for driving innovation in security solutions such as voice pattern technology. Business executives, mid-level managers, and entrepreneurs play a pivotal role in championing the adoption of emerging technologies and fostering a culture of security awareness within their organizations. By prioritizing investments in cybersecurity and embracing cutting-edge solutions, leaders can protect their businesses from evolving threats and ensure long-term success.
Strategic partnerships with technology vendors, research institutions, and government agencies can also accelerate the development and adoption of voice pattern technology. By collaborating with external stakeholders, organizations gain access to additional expertise, resources, and funding opportunities, enabling them to stay at the forefront of security innovation. Strategic alliances facilitate knowledge sharing, promote industry standards, and drive collective efforts to address cybersecurity challenges.
Looking ahead, the integration of voice pattern technology into broader security ecosystems holds immense promise for businesses in Saudi Arabia and the UAE. By combining biometric authentication with other advanced technologies such as AI and blockchain, organizations can create multi-layered security frameworks that adapt to emerging threats and protect against unauthorized access. With visionary leadership and strategic partnerships, businesses can secure their future in an increasingly digital world.
#VoicePatternTechnology #SecuritySolutions #BiometricAuthentication #ArtificialIntelligence #ChangeManagement #ManagementConsulting #EmergingTechnologies